Offset-X: The Future of Conflict and the New Requirements of Defense
SCSP’s Defense Interim Panel Report
Hello, I’m Ylli Bajraktari, CEO of the Special Competitive Studies Project. In this edition of our newsletter, we summarize our first interim panel report. It’s focused on the future of conflict and warfare, and how best can the United States military prepare and position for such a future.
In this month’s edition of 2-2-2, Senior Director of Defense Justin Lynch and Associate Director of Defense Luke Vannurden summarize SCSP’s first panel report.
SCSP Defense Panel Releases Interim Panel Report
The Defense Panel recently released its Interim Panel Report (IPR): The Future of Conflict and the New Requirements of Defense. This IPR is the first of six interim reports from the overall work that SCSP has conducted over the past year and that was summarized in our Mid-Decade Challenges to National Competitiveness report published on September 12, 2022.
We also encourage you to watch Deputy Secretary of Defense, Dr. Kathleen Hicks, discuss some of the themes from our report at the SCSP Global Emerging Technology Summit, as well as a panel discussion on the future of warfare by Robert O. Work, Nadia Schadlow, William “Mac” Thornberry, Stanley McChrystal, and August Cole.
Reach out to info@scsp.ai with any questions!
THE FUTURE OF CONFLICT AND THE NEW REQUIREMENTS OF DEFENSE:
Highlights from the Defense Panel IPR
Before the end of this decade, the United States and its allies will face a new kind of warfare. This is not to say that war by 2030 is inevitable. Rather, should a war occur, its character will be unlike anything America and its allies have ever experienced. Warfare and peace are changing under pressure from three key drivers - (1) advanced and emerging technologies, including artificial intelligence, (2) innovative operational concepts for employing them, and (3) intensifying geopolitical rivalries. We already see attributes of this new character of conflict in Ukraine. But they are just the beginning. These changes will only continue to accelerate and intensify, particularly under pressure from technological disruptions, and can be expected to play out at both the strategic and operational levels.
Strategically, the most consequential change is the morphing of the persistent competition into persistent conflict, even if still under the level of armed clashes. Adversaries’ cyber attacks, disinformation operations, theft of intellectual property, and sabotage against the United States, are all referenced in the recently published National Security Strategy, and all carry the consequences of a modern day conflict, though obviously not as violent as the current Russian invasion of Ukraine. By blurring the line between war and peace, and by involving some of the highest stakes of national interests, they are also increasing the likelihood of a great power war - one that runs a high risk of devolving into a protracted war of political will, industrial capacity, and innovation ecosystem - the second most consequential change in character. Such a war would be unlike any of the previous ones that America has been involved in, both in potential magnitude and terrifying precision - the third most consequential change. For most Americans, war has been something that occurs elsewhere, fought by an all-volunteer force expected to suffer less and less casualties from one campaign to another. Today’s cyberweapons, hypersonic missiles, or disinformation campaigns threaten to bring war to the doorstep of most Americans. The digital exhaust we leave online everyday with our shopping habits, dating preferences, social networking, and career links is now accessible, in bulk, for our adversaries to collect and turn into micro-targeting packages. While this targeting may primarily take the form of denigration campaigns, and psychological pressure, it can also include biological warfare, traditional targeted killings, or even strikes from global platforms. And, finally, our adversaries cannot be expected to be ethically and legally constrained in the application of emerging technologies in warfare.
At the operational level, the two most consequential changes to conflict will likely be in how we perceive the environment, and in how combatants hide from and find opposing forces. Mass data production and collection, sifted and analyzed by artificial intelligence, are increasing the availability of data points for analysis, giving leaders much greater awareness over the battlefield. As the battlefield becomes more transparent, including in the once opaque space and undersea domains, and tools of attack become faster and more precise, the hinder-finder contest is changing fundamentally. If militaries become more easily detected and rapidly destroyable, it will become increasingly difficult to employ operational surprise, mass troops, or not preemptively act.
The People’s Liberation Army’s Plan for Victory. How may our competitors and adversaries be preparing for such changes in warfare? Expectedly, the People’s Republic of China (PRC) poses a particularly sharp threat with its determination to harness these changes to erode or even leapfrog the United States’ military strengths. China’s military, the People’s Liberation Army (PLA), has closely studied the American way of war for the last three decades, and has single-mindedly focused on investments, capabilities, and plans to defeat the U.S. military. China’s leader, Xi Jinping, on Sunday promised to “work faster to modernize military theory, personnel and weapons,” and to “enhance the military’s strategic capabilities.” The PLA calls its current concept to defeat the U.S. military systems destruction warfare that seeks to render our military blind, deaf, and unable to communicate, resupply, and attack.
In pursuit of a theory of victory for a potential confrontation today, the PLA has also sought to chart a path to leapfrog the United States for a potential confrontation of tomorrow. By capitalizing on the growing capabilities of AI, big data, advanced computing, 5G, and supporting technologies, the PLA intends to shift from informatized warfare to intelligentized warfare. By becoming the first movers in a new way of war, they hope to leapfrog the United States and become the world’s dominant military power.
Neither despair nor hubris. The consequences of the status quo are severe: a shift in the balance of power globally; a direct threat to the peace and stability that the United States has underwritten for nearly 80 years in the Indo-Pacific – the most economically, technologically, and resource-critical region of this century; and relinquishing the command position to shape the direction of the global economy. Russia’s invasion of Ukraine will be the end of the beginning of a trend, rather than a historical anomaly. Great and middle power wars will be far more likely to return, and with it, all of the horrors of the world wars.
The United States should respond neither with despair nor hubris. The American military has demonstrated an ability to develop new capabilities and employ them in new and innovative ways to confound adversaries. Moreover, the United States retains significant military-technological advantages – demonstrated consistently on the battlefield – that it can continue to leverage: demonstrated experience in combined arms, expeditionary, and networked operations; experienced and empowered leaders at the most tactical level; demonstrated ability to conduct expeditionary logistics on scale and across the globe; allies and partners worldwide that amplify and enable American power; and a democratic and resilient society that empowers the individual, fosters creativity, and is governed by independent institutions.
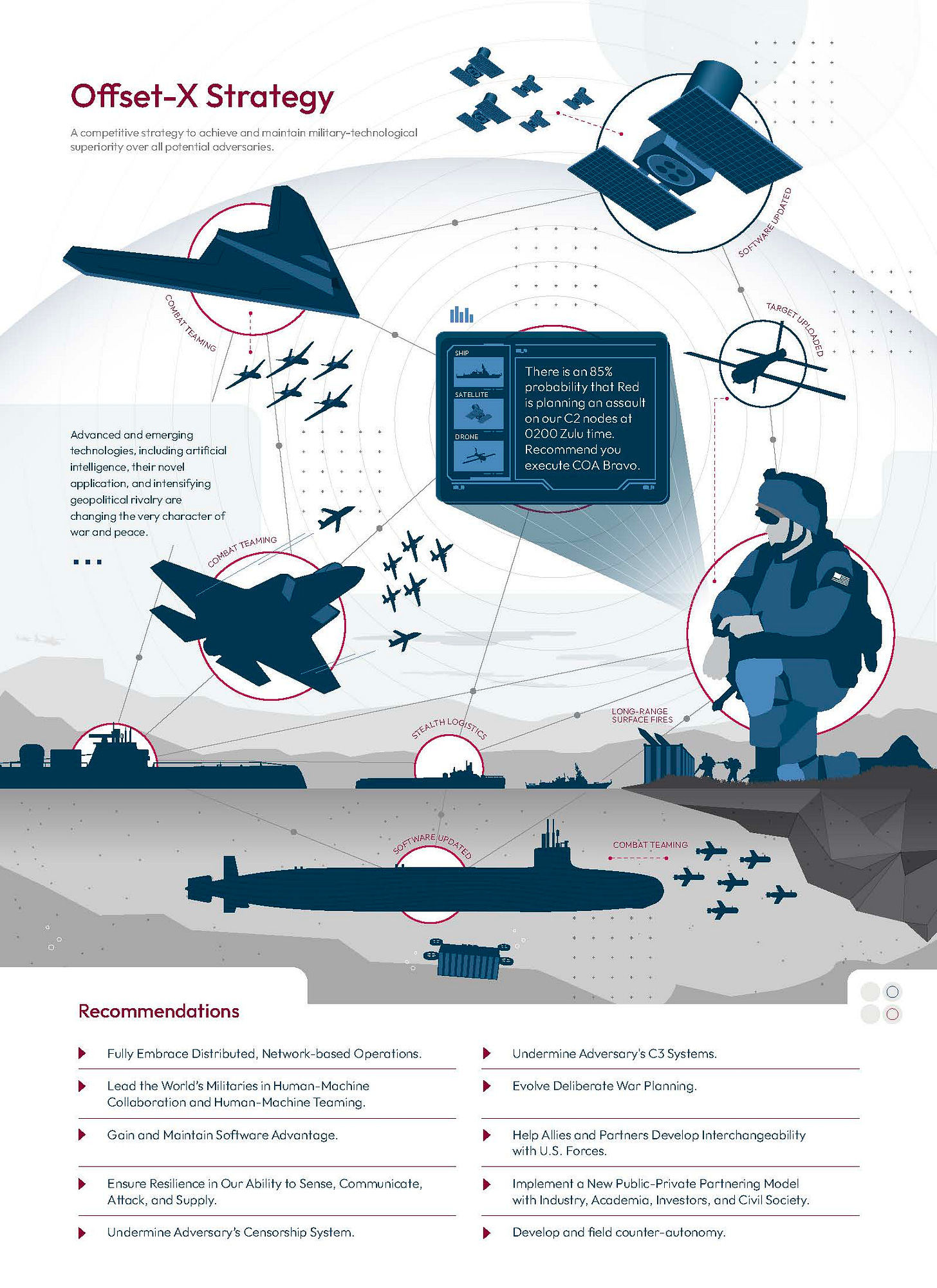
But changes will have to be made, and done so quickly. Where our military overmatch has been compromised, we can rebuild it. Where our self-confidence has been shaken, we can regain it. Our Interim Panel Report on Defense proposes a new, tech-enabled competitive strategy - that we call Offset-X - that could enable this transition.
OFFSET-X STRATEGY
In decades past, when the United States faced significant changes in the character of conflict and similarly ambitious rivals, it turned to offset strategies to negate or even leapfrog those advantages. The United States has pursued three offset strategies. The first was the expansion of U.S. nuclear capabilities in the 1950s and 1960s to counter Soviet conventional military superiority in Europe. The Second Offset Strategy was designed in the 1970s by the Department of Defense to destroy Soviet conventional forces without using nuclear weapons to prevent them from overrunning Western Europe. These capabilities evolved into the U.S. precision strike regime, battle networks, and deep strike operational concepts put on display in the First Gulf War. The Third Offset Strategy began in the middle of last decade and centered around investing in human-machine teaming and autonomy to overcome the PLA’s advantages in the Western Pacific.
Offset-X is an attempt at intellectual continuity of these past, successful offsetting strategies. The initiatives we outline in the report and below are, by no means, a comprehensive or definitive list of actions. And no offset strategy against China should be treated as set in stone. But together, these actions embody a competitive strategy to achieve and maintain military-technical superiority over all potential adversaries, but one that needs to be regularly reassessed against adversaries' adaptations and emerging technologies.
The strategy is focused on three goals: (1) to invalidate the defense investments the PRC has made to defeat the U.S. military; (2) to generate U.S. capabilities that, in war, would increase the political and economic cost of war for the PRC while reducing ours; and (3) to generate a spectrum of U.S. military options that confound and inject uncertainty into the PLA’s planning.
The strategy we propose includes ten specific recommendations:
1. Fully Embrace Distributed, Network-Based Operations to Survive, Out-Maneuver, and Overwhelm Adversaries. Confronted with adversaries that value rigid hierarchies and have invested in capabilities that could protect them against concentrated, frontal assaults, the U.S. military should continue to develop and experiment with how it will employ smaller, highly-connected, and organically resilient, multi-domain units. Units would operate in a distributed fashion, inside and outside an adversary’s envisioned battlespace, leveraging U.S. global posture and access arrangements with partners and allies. Such a network would generate significant dilemmas for adversaries by subverting their operations, creating multiple attack vectors, and operating with greater adaptability than more hierarchical systems. They are also more resilient, and able to preserve decision-making and attack capabilities while experiencing damage that would degrade a hierarchical system much more.
2. Lead the World’s Militaries in Human-Machine Collaboration and Human-Machine Teaming. Essential to the concept of distributed, but highly-networked forces will be an extensive network of low-cost sensors, satellites, and reconnaissance platforms, as well as large numbers of attritable unmanned systems operating at sea, in the air, in space, and on the ground to expand attack surfaces and absorb lethality. Employing them effectively, however, will require mastering human-machine cognitive collaboration (HMC) and human-machine combat teaming (HMT).
HMC enables military leaders to improve and accelerate planning, and optimize decision-making. HMT, which focuses on the accomplishment of complex tasks in physical spaces, could enable the U.S. military to generate and employ mass in contested environments in a way that reduces the risk to humans, including the risk of collateral damage. Today, in most cases, many warfighters collectively control one platform, such as a ship. While this relationship is unlikely to vanish, another human-machine relationship is developing: AI-powered architectures that leverage the contextual awareness and complex reasoning of human operators to manage large numbers of autonomous and semi-autonomous unmanned systems, also known as swarms. Another, less discussed relationship, is one wherein a small number of warfighters, skilled at software development, could create an application that optimizes the performance of many warfighters or machines down the line.
Lower-cost, easier-to-manufacture, AI-enabled machines, would allow the U.S. military to develop operational concepts that leverage advanced systems to permit operators and machines to overcome complex challenges. Massed machines, assigned tasks by their human teammates, could overwhelm traditional defenses, often at a relatively smaller cost in human casualties compared to more traditional offensive operations. Machines could also serve as the “eyes and ears” of their human teammates, particularly in urban warfare, by helping them gain more information about their environment and taking risks in their place.
3. Gain and Maintain Software Advantage. A military’s ability to deploy, employ, and update software, including AI models, faster than its adversaries is likely to become one of the greatest determining factors in relative military strength. Software is now integral to every component of decision-making and operations, from sensing a target (sensor software), to decision-making (aggregation and analysis), targeting (weapons guidance system), and battle damage assessment. The importance of software will only continue to increase. As militaries around the world increasingly rely on platforms with advanced computing capacities, and supplement or even replace some functions of human service members with algorithms, software superiority will become an even greater determining factor. The quality of software will determine a military’s primacy in collecting and analyzing information, developing an operating picture, thwarting enemy attacks, identifying opportunities in time and space to most effectively attack, and helping with target selection and servicing. The side that adapts faster and demonstrates the greatest agility, to include rapidly updating fielded software and AI models, will gain a significant tactical and operational advantage
4. Ensure Resilience in Our Ability to Sense, Communicate, Attack, and Supply. In a conflict with China, the PLA’s concept of system destruction warfare would indicate that one of the PLA’s opening moves will be directed at U.S. forces' ability to see, track, and locate them precisely. Simultaneous or follow-on attacks will likely target the ability of U.S. military leaders to command and control their forces. Additional attacks will almost certainly be aimed at the U.S. military’s ability to logistically sustain its operations.
To avoid paralysis, the U.S. military needs to build resilience, and where necessary, redundancies across every link and node of its operations. Resilience can come from acquiring and using very large numbers of low-cost and attritable platforms that would support intelligence collection, communication, expeditionary logistics, and attack – especially during the opening days of a campaign. Operational resilience also requires strategic resilience, which will be heavily dependent upon our ability to harden the nation’s critical infrastructure from cyber-attacks.
5. Undermine Adversary’s Censorship System. The United States needs to continue developing technologies that allow Chinese citizens to bypass the Chinese government’s censorship system. Authoritarian regimes are brittle, relying more on information control than buy-in to maintain domestic stability. As such, they are vulnerable to operations that allow their populations to more easily and consistently bypass censorship systems, access information other than state propaganda, and create viral narratives that run contrary to their government’s message. In the context of war, such operations – including AI-enabled messaging that can circumvent censorship – have the potential to distract authoritarian regimes by increasing their focus on domestic security.
6. Undermine Adversary Command Systems. The United States should also consider how it can subvert the effectiveness of adversary conventional command, control, and communication (C3) systems. If the United States were to disrupt or cripple the PLA’s C3 systems, it would cause disarray among the ranks of the PLA and desync its operations, preventing it from massing effects against U.S. forces.
7. Evolve Deliberate War Planning. Traditionally, the Department of Defense’s (DoD) deliberate war planning is based on the existing inventory of capabilities and forces. This approach to deliberate war planning, however, does not factor in the state of the defense industrial base and its ability, or lack thereof, to surge production of munitions or platforms, potentially creating serious strategic risks, particularly in the event of high-intensity operations that rapidly consume existing inventory of munitions and assets, or in the event of a protracted conflict. It also limits the development of innovative concepts and reduces the ability of Combatant Commanders to influence the development of new capabilities. Therefore, the Defense Department should seriously consider evolving its deliberate war planning guidance to consider the health and resilience of the defense industrial base and the full potential of the national security innovation network.
8. Help Allies and Partners Develop and Maintain Interoperability and Interchangeability with U.S. Forces. As the United States continues to modernize its military forces, there is a risk that a capabilities gap between the United States and its allies could become a serious impediment to combined operations. The United States must address these challenges if it is to capitalize on one of its most enduring asymmetries against China – its network of alliances and partnerships. In the near term, a promising action could be the establishment of a multilateral intelligence, surveillance, and reconnaissance network to improve coalition awareness in peacetime, and enable a more rapid transition from crisis to conflict during wartime. Another action could be the development of a Joint and Combined All Domain Command and Control (JCADC2) architecture with auto-interoperability functions. This would be the multilateral expansion of the current U.S.-only Joint All-Domain Command and Control (JADC2) concept. The U.S. Government must accept far greater risks in information sharing and transfer of technologies to make this successful.
9. Implement a New Public-Private Partnering Model Between the U.S. Government, Industry, Academia, Investors, and Civil Society. The United States must make a concerted effort to restore the level of collaboration between the government, industry, and academia, and to accelerate the adoption of commercial technology by the DoD. Just as importantly, collaboration must also extend to private investors and civil society. If the United States is able to unite all five stakeholders to pursue specific goals, America’s dynamic market capitalist system and innovative commercial sector is much more likely to prevail over the long term. If not, the United States risks ceding critical ground to China.
10. Develop Counter-Autonomy. As the U.S. military integrates more AI, human-machine teaming, and autonomy, adversaries can be expected to do the same. The U.S. military should, therefore, develop capabilities and concepts for countering adversary autonomy. In the near term, the focus of U.S. counter-autonomy efforts could include identifying means and generating access to take over adversaries’ AI-enabled systems to extend our sensing deep inside their territory and within its decision-making. During conflict, counter-autonomy efforts could include actions to manipulate the data or outputs of adversarial AI-enabled systems so as to inject mistrust between their forces and their machines, degrading the performance of their AI-enabled and autonomous systems, or destroying them entirely through kinetic or non-kinetic means.
Operationalizing the Offset-X Strategy
The ten recommendations outlined above embody a competitive strategy to lay the groundwork for achieving and maintaining military-technical superiority over all potential adversaries. Significant prototyping, experimenting, and wargaming are needed to validate the applicability and effectiveness of these technologies for specific operational demands. The precise mix of emerging technologies and capabilities will yet need to be determined to address the changing character of warfare and peace. But as with previous successful offset strategies, the national and DoD pursuit and mastery of emerging technologies and innovation can enable the crafting of new operational concepts that can be tailored to meet specific military challenges.