The Next Pandemic Will Be Digital
Open Source Hardware and New Vectors of National Cybersecurity Risk
Hello, I’m Ylli Bajraktari, CEO of the Special Competitive Studies Project. In this edition of the 2-2-2, SCSP Senior Fellow Rick Switzer, who is on a one-year sabbatical from the Department of State, discusses the national cybersecurity risks of open source hardware.
Prior to joining SCSP, Rick was a State Department visiting professor at the National Intelligence University teaching graduate courses on China’s economy and innovation system. Rick also served as a member of the Secretary of State’s Policy Planning Council. From 2018 to 2019, he was a Senior State Department Advisor to the Department of Defense working with the Air Force and the Army. Preceding that he was the Environment, Science, Technology and Health Minister Counselor at Embassy Beijing, the largest science section in the world. Prior to joining government, Rick co-founded a wireless technology start-up and also conducted innovation policy research at the University of California.
The views in this newsletter are the author's own and based on research he conducted prior to and during his sabbatical with SCSP. These views are not attributable to SCSP, the SCSP Board, or its staff.
You nervously check your smartphone for the fifth time today. Your bank account – and much of the Internet – is still down.
It’s been a week since the crisis began. Cable news is flooded with reports of protests and looting at grocery stores around the nation. With stores unable to process digital financial transactions, customers without cash on hand cannot buy food and water. Lines outside banks stretch for hours as customers frantically withdraw cash. Mayors of Los Angeles, Chicago, Detroit, and other major cities have imposed curfews, but reports of widespread violence have left Americans anxious and panicked.
What began as outages at a series of regional banks has taken down much of the nation’s digital infrastructure, leading to severely limited internet access. Financial transactions have ground to a halt. The attacks were traced to a cloud service provider for regional banking firms, but outages now appear to be more widespread, covering close to 40 percent of all cloud storage services across the country. The Department of Homeland Security and private sector cybersecurity firms have scoured affected data centers for the cause, but have come up empty so far. In the White House Situation Room, the President is growing impatient, demanding answers.
Government investigators finally discover the issue: a hardware-based on-off switch embedded in a series of voltage-regulating chips. The attackers flipped billions of these switches all at once, preventing logic chips from connecting to the storage chips in cloud servers. Tracking the exact source of the chips has proven difficult, as nearly all of the affected hardware are inexpensive electronics components based on open hardware standards and sourced from the cheapest available supplier. Virtually all components are from hundreds of factories dispersed across China. Initial estimates show it will take 12-18 months to identify, remove, and replace all the corrupted hardware. Yet it is unclear whether this strategy is feasible, as the only sources for replacing the components are the same factories where the original chips were built. The President’s advisors inform him that the total cost of the crisis may exceed trillions of dollars in damages and lost GDP, and the broader damage to Americans’ wellbeing and the nation’s social cohesion is incalculable.
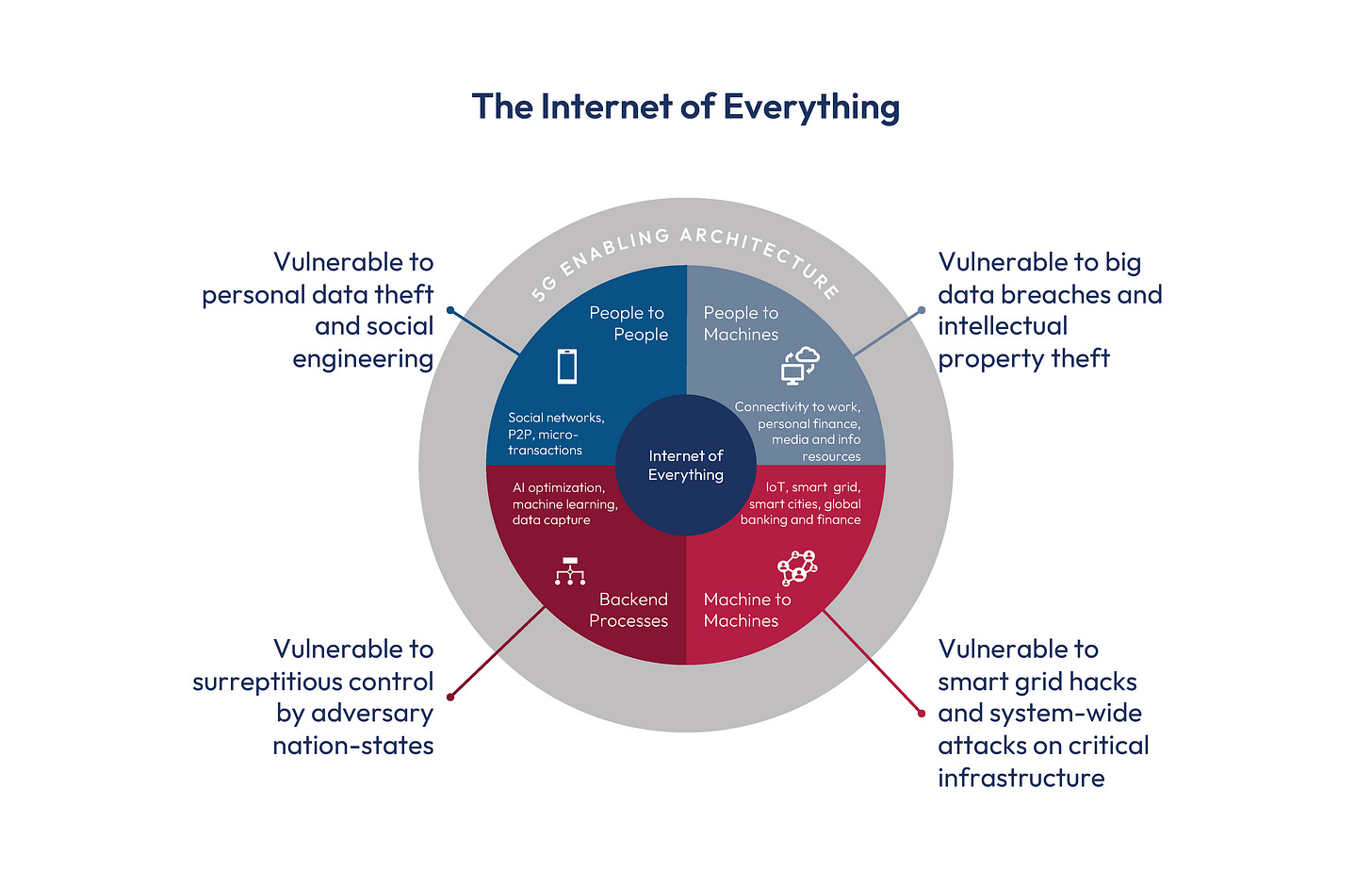
Over the past ten years, open source technology has rapidly grown in popularity, unlocking tremendous economic value. Attention to date has focused mostly on open source software. GitHub, for example, is an open source database where code is posted for anyone to use. Today, however, all kinds of computer hardware are also being built with open source designs, including semiconductors, routers, and Internet of Things (IoT) devices. Yet open source hardware also presents significant challenges for national security. As billions of interconnected smart devices blur the lines between the physical and digital worlds, we risk creating new vulnerabilities that nation-state actors could exploit.
With the rapid growth of the Internet of Things and its application to critical infrastructure, widespread adoption of open source hardware will create new attack vectors for nation-state actors. Unlike traditional, software-based cyberattacks, ‘hardware trojans’ allow attackers to insert vulnerabilities directly onto a chip or into a router. Even when vulnerabilities can be detected, the generic nature of open source hardware renders it nearly impossible to trace a vulnerability back to its source. If a nation-state were to use its market dominance to insert hardware trojans across the entire ecosystem, it would be nearly impossible to stop. As the world’s leading producer of legacy chips – used in many everyday smart devices – and generic ‘white box’ electronics, the People’s Republic of China (PRC) is best positioned to capitalize on these factors.
The Internet of Things, cloud computing, and advanced wireless networks are unlocking efficiency gains across society, but potential vulnerabilities must be accounted for.
What Is Open Source Hardware?
Open source hardware is computer hardware with a public design that anyone can freely study, modify, make, use, or sell. Given that all players are free to use open source designs, someone might note, why should this be of concern to the U.S. Government, or any government for that matter? Put simply, open source hardware is the future, and its adoption will be massively disruptive. The open source revolution will lead to the rise of cheap, interchangeable hardware, driving down costs for the world’s largest software, networking, and internet platform companies. As with other transformational technology trends, current market leaders are likely to face disruption and major challenges to their business model.
Three major open source hardware initiatives exist today: RISC-V, an open source chip architecture; the Open Compute Project (OCP), a collective of cloud storage providers working to bring open source hardware to the data center; and open network architectures, particularly Open Radio Access Network (ORAN) technology, which involves building open source hardware for advanced networks like 5G. Taken together, these efforts cover most of the communications and technology landscape. Key industry leaders have embraced RISC-V, OCP, and ORAN, positioning them to shape the rollout of cutting-edge digital infrastructure around the world.
RISC-V was developed at University of California Berkeley as a tool meant to simplify chip design via an open source architecture. In 1980, funding from the Pentagon’s Defense Advanced Research Programs Agency (DARPA) provided critical funding that helped build the first RISC-based processors. RISC-V launched at Berkeley in 2010. Five years later, the RISC-V Foundation was established with the Chinese Academy of Sciences and U.S.-based multinational firms like Google and IBM among its founding members. The organization moved its headquarters from the United States to Switzerland in 2019 to ensure that members – specifically firms from the PRC – would not be subject to U.S. tech transfer restrictions, per the organization’s CEO. Board members today include a who’s who of tech companies from the United States, China, and elsewhere, from U.S. tech companies to PRC national champions Huawei, Alibaba, and Tencent.
What does the open source hardware revolution look like in practice? In 2019, U.S.-based telecoms giant AT&T released specifications for a generic ‘white box’ router, based upon OCP’s open-router design. These generic routers would replace traditional U.S.-based suppliers like Dell or Cisco. Since then, AT&T has announced its plans to install more than 60,000 generic, open source routers across its network in support of its 5G plans – the company estimates that it will need 250,000 to 300,000 to meet its U.S.-based 5G network demands. Commodity producers from Taiwan and China currently produce all of these white-box routers. These routers will eventually form the infrastructure that will enable not just phones and tablets to connect to its mobile 5G network, but also new technologies like autonomous vehicles, drones, augmented reality and virtual reality systems, smart factories, and more.
Open Source Hardware, the Internet of Things, and Cyberattacks
The open source revolution is happening in parallel with the ongoing revolution in cloud computing and the Internet of Things, which is embedding billions of always-on smart devices throughout our society. According to the International Data Society, nearly 42 billion IoT devices could be deployed by 2025. These networks of devices touch every aspect of modern life, from factories, logistics centers, power grids, and water systems to hospitals, traffic systems, and smart homes.
Embedded microelectronics power critical infrastructure sectors on which modern life depends. With the rise of open source hardware, these sectors may be at risk.
Unlike traditional cyber attacks – which stem from vulnerabilities in computer code – open source hardware creates new attack vectors that are more difficult to resolve. There are several reasons for this. First, cyber vulnerabilities are much more difficult to manage when hardwired into a chip or router, rather than buried in lines of computer code. To make matters worse, building hardware with an open source design means industry players no longer carry the same reputational risk associated with keeping their products secure. The generic nature of open source hardware also leaves the original sources of production unclear. This creates new supply chain risks by rendering it difficult, if not impossible, to determine whether a piece of hardware was produced in Mexico or China. Existing efforts to guarantee the security of open source hardware leave unanswered questions. If left unexamined and unregulated, the United States could find its critical infrastructure compromised and dependent on an adversarial power.
Developments in open source hardware are creating new cybersecurity threat vectors for which we are unprepared.
Beijing’s Open Source Ambitions
The Chinese government sees open source hardware as key to its quest to reduce its technology dependence on the United States and other countries. China’s government has set up its own version of the Open Compute Project, the Open Data Center Committee, and PRC tech giant Baidu is working directly with Meta and Microsoft to develop sophisticated AI chips. Ahead of the United States’ recent moves to restrict PRC companies’ access to advanced chips produced by non-Chinese companies, Beijing also helped found the “China RISC-V Alliance,” which aims to boost the adoption of open source architecture in China and reduce reliance on Western-controlled chips. The first resulting special-purpose chips are already in production by Chinese companies. Beyond end-running U.S. export controls and leapfrogging ahead in semiconductor design, Beijing’s interests may also stem from a desire to embed cybersecurity flaws at the design phase.
The PRC is currently the only nation state with the global microelectronics manufacturing industrial base, technical sophistication, and ministries powerful enough to fully exploit this growing risk to global digital infrastructure. PRC officials are not subject to the same constraints and accountability mechanisms as their peers in rule-of-law societies, and law enforcement in China is subject to the Party’s whims. Given the PRC’s central position in the global electronics supply chain, an open source production ecosystem could grant Beijing the ability to access and control much of the world’s digital infrastructure.
What Should We Do?
At present, the United States is not organized to prevent the PRC from weaponizing the open source hardware revolution should it choose to do so. Open source hardware is poorly understood outside technology circles, including within the U.S. Government. Washington lacks a policy framework to address the national security challenges that open source hardware could pose.
Given these real and growing issues, we argue for a strategy that mitigates this risk at the source. Sourcing from trusted suppliers – which we argue means restricting the use of core digital infrastructure components manufactured in countries of concern – is a key step to ensure that chips, circuit boards, and other hardware are not corrupted by bad actors. In other words, an approach that would wall out PRC producers, using tools like content requirements, due diligence, and market access restrictions in critical infrastructure sectors, is required. To implement this strategy, U.S. authorities should:
Organize to respond to potential threats posed by open source hardware produced in countries of concern;
Develop robust security standards for open source hardware;
Increase disclosure requirements for U.S. firms;
Consider blocking imports of open source hardware from countries of concern; and
Increase R&D funding for hardware-based cybersecurity.
For more details, see the full version of The Next Pandemic Could be Digital: Open Source Hardware and New Vectors of National Cybersecurity Risk here.
Additional Reading: A Techno-Industrial Strategy Thought Experiment
As part of SCSP’s ongoing effort to design a new techno-industrial strategy, Senior Fellow Rick Switzer also recently produced a white paper on how to complement the CHIPS Act and drive the revitalization of the U.S. microelectronics industry. CHIPS funding can shore up the U.S. innovation ecosystem and serve as a down payment to build several high-end production facilities, but to mitigate security risks and reduce America’s reliance on chips produced in East Asia, the United States needs to drive a large-scale reshoring.
One of the greatest challenges for the current effort is how to make the new federal dollars “crowd-in” private capital. As manufacturing chips becomes more expensive and complex, increased risk has driven away private investment. Over the past decade, for example, funding for semiconductor startups has dropped from nearly 8 percent of venture capital investment to less than half a percent.
This paper proposes a solution in the form of a Semiconductor Industry Investment Fund, or Si² Fund (pronounced SI Squared). This “fund-of-funds” proposes channeling federal dollars as matching seed capital to incentivize private investment into domestic semiconductor manufacturing. The fund would overcome the biggest obstacles to realizing the CHIPS’ goals by first, de-risking private investment and increasing returns to investors willing to put capital to work in support of national security goals, and second, providing a mechanism to extend the scale and life of the CHIPS effort beyond the current five-year plan, boosting America’s long-term competitiveness.
Read the full paper, titled The Si² Fund: Building a Microelectronics Fund of Funds, here.